Introduction
In this journal I am going to discuss my steps in setting up docker in Proxmox v8.1.3. For this I will create a Debian container, specifically v12. My goal was to gain familiarity of deploying docker containers and broading my experience with virtualization.
IMPORTANT NOTE: If you have any intention of setting up NFS shares on the host OS to be accessed by containers, you will need to setup Docker/Portainer using a VM rather than a Container. Non-privileged containers do no have access to NFS shares, and privileged containers cannot run Docker (due to keyctl requirement). Ultimately if you wish to use NFS with your containers and host machine, you will have to start with a VM. The following steps are the same, instead of setting up a container you will setup a VM e.g., Ubuntu Server. Once in this configuration I recommend adding NFS shares to the hosts /etc/fstab and then using a bind for the container.
Creating a Container
The first thing to do is create the container. For this we need to use a template: from your local storage on your Proxmox instance, choose "Templates" and search for Debian (again I am using Debian 12). Download this template and then create "CT Container".
Configure Container
Next step is to configure your container settings:
Hostname
Password (for root)
Choose your template of choice (Debian 12 for me)
Continue through the various sections. Please Note: I had issues with he container displaying a blank screen after starting, with no login prompt. To solve this issue I had to set IPv6 to static, however I did not provide an address, just set it to static.
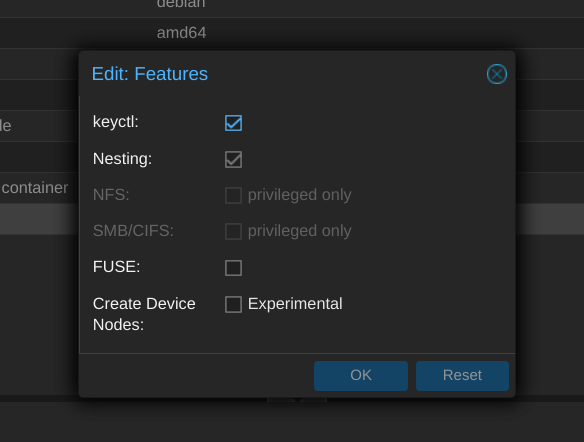
Before starting the container edit the options and enable keyctl. Here are some details on why this should be enabled:
keyctl
For unprivileged containers only: Allow the use of the keyctl() system call. This is required to use docker inside a container. By default unprivileged containers will see this system call as non-existent. This is mostly a workaround for systemd-networkd, as it will treat it as a fatal error when some keyctl() operations are denied by the kernel due to lacking permissions. Essentially, you can choose between running systemd-networkd or docker.
from: man pct
Start the container and then login with root and your defined password.
Update the Container and Install curl
apt update
apt upgradeInstall curl:
apt install curl -yInstalling Docker
To installer Docker into our Debian container I am going to user a script directly from Docker's website - there is a certainly level of trust here, executing a script from an unknown source, I recommend you review the script for your knowledge and comfort.
curl -sSL https://get.docker.com/ | shThis concludes the setup of Docker, and you should be able to move forward and create containers if you are familiar with the process. For me, I am going to install Portainer, so I have a GUI for Docker management.
Install Portainer
Use the following commands to install Portainer:
docker run --restart always -d -p 9000:9000 -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ceAccess Portainer
To user portainer, navigate to the container IP address, and use the port 9000.
Updates:
I personally had a problem stopping the containers from command line, even as root. The command to stop all containers is as follows:
sudo docker stop $(sudo docker ps -a -q)However, to make this work I needed change the permissions on the socket file, first check them:
sudo ls -l /var/run/docker.sockThen I changed them to my local user:
sudo chown macleod:docker /var/run/docker.sock
sudo chmod 660 /var/run/docker.sockAnd also, I made sure to add my user to the docker group:
sudo usermod -aG docker macleod